156-315.80 | Renewal Check Point Certified Security Expert - R80 156-315.80 Actual Test
It is impossible to pass Check-Point 156-315.80 exam without any help in the short term. Come to Pass4sure soon and find the most advanced, correct and guaranteed Check-Point 156-315.80 practice questions. You will get a surprising result by our Update Check Point Certified Security Expert - R80 practice guides.
Also have 156-315.80 free dumps questions for you:
NEW QUESTION 1
How often does Threat Emulation download packages by default?
- A. Once a week
- B. Once an hour
- C. Twice per day
- D. Once per day
Answer: D
NEW QUESTION 2
Packet acceleration (SecureXL) identifies connections by several attributes- Which of the attributes is NOT used for identifying connection?
- A. Source Address
- B. Destination Address
- C. TCP Acknowledgment Number
- D. Source Port
Answer: C
Explanation:
https //sc1.checkpoint.com/documents/R77/CP R77_Firewall_WebAdmm/92711.htm
NEW QUESTION 3
What is the purpose of extended master key extension/session hash?
- A. UDP VOIP protocol extension
- B. In case of TLS1.x it is a prevention of a Man-in-the-Middle attack/disclosure of the client-servercommunication
- C. Special TCP handshaking extension
- D. Supplement DLP data watermark
Answer: B
NEW QUESTION 4
Which TCP-port does CPM process listen to?
- A. 18191
- B. 18190
- C. 8983
- D. 19009
Answer: D
NEW QUESTION 5
What statement best describes the Proxy ARP feature for Manual NAT in R80.10?
- A. Automatic proxy ARP configuration can be enabled
- B. Translate Destination on Client Side should be configured
- C. fw ctl proxy should be configured
- D. local.arp file must always be configured
Answer: D
NEW QUESTION 6
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- A. The rule base can be built of layers, each containing a set of the security rule
- B. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
- C. Limits the upload and download throughput for streaming media in the company to 1 Gbps.
- D. Time object to a rule to make the rule active only during specified times.
- E. Sub Policies ae sets of rules that can be created and attached to specific rule
- F. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule.
Answer: D
NEW QUESTION 7
What is considered Hybrid Emulation Mode?
- A. Manual configuration of file types on emulation location.
- B. Load sharing of emulation between an on premise appliance and the cloud.
- C. Load sharing between OS behavior and CPU Level emulation.
- D. High availability between the local SandBlast appliance and the cloud.
Answer: B
NEW QUESTION 8
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were
dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
- A. fw ctl multik dynamic_dispatching on
- B. fw ctl multik dynamic_dispatching set_mode 9
- C. fw ctl multik set_mode 9
- D. fw ctl multik pq enable
Answer: C
NEW QUESTION 9
Which one of the following is true about Threat Emulation?
- A. Takes less than a second to complete
- B. Works on MS Office and PDF files only
- C. Always delivers a file
- D. Takes minutes to complete (less than 3 minutes)
Answer: D
NEW QUESTION 10
On R80.10 the IPS Blade is managed by:
- A. Threat Protection policy
- B. Anti-Bot Blade
- C. Threat Prevention policy
- D. Layers on Firewall policy
Answer: C
NEW QUESTION 11
Which of the following Check Point processes within the Security Management Server is responsible for the receiving of log records from Security Gateway?
- A. logd
- B. fwd
- C. fwm
- D. cpd
Answer: B
NEW QUESTION 12
Why would an administrator see the message below?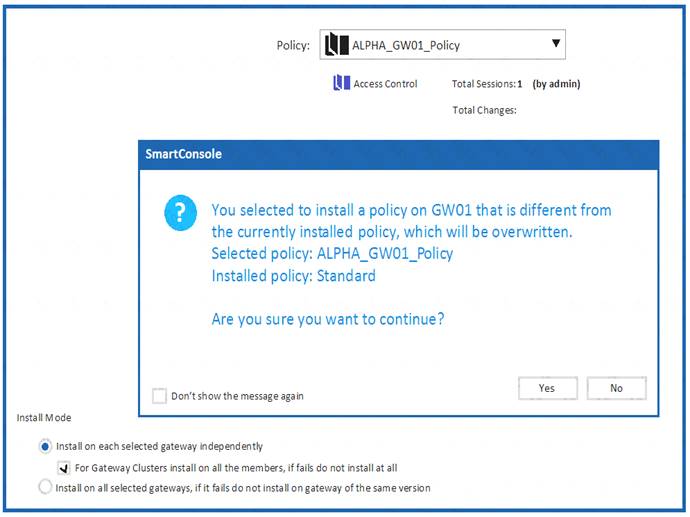
- A. A new Policy Package created on both the Management and Gateway will be deleted and must be backed up first before proceeding.
- B. A new Policy Package created on the Management is going to be installed to the existing Gateway.
- C. A new Policy Package created on the Gateway is going to be installed on the existing Management.
- D. A new Policy Package created on the Gateway and transferred to the Management will be overwritten by the Policy Package currently on the Gateway but can be restored from a periodic backup on the Gateway.
Answer: B
NEW QUESTION 13
Session unique identifiers are passed to the web api using which http header option?
- A. X-chkp-sid
- B. Accept-Charset
- C. Proxy-Authorization
- D. Application
Answer: C
NEW QUESTION 14
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
- A. Logging has disk space issue
- B. Change logging storage options on the logging server or Security Management Server properties and install database.
- C. Data Awareness is not enabled.
- D. Identity Awareness is not enabled.
- E. Logs are arriving from Pre-R80 gateways.
Answer: A
NEW QUESTION 15
To fully enable Dynamic Dispatcher with Firewall Priority Queues on a Security Gateway, run the following command in Expert mode then reboot:
- A. fw ctl multik set_mode 1
- B. fw ctl Dynamic_Priority_Queue on
- C. fw ctl Dynamic_Priority_Queue enable
- D. fw ctl multik set_mode 9
Answer: D
NEW QUESTION 16
The log server sends what to the Correlation Unit?
- A. Authentication requests
- B. CPMI dbsync
- C. Logs
- D. Event Policy
Answer: D
NEW QUESTION 17
What SmartEvent component creates events?
- A. Consolidation Policy
- B. Correlation Unit
- C. SmartEvent Policy
- D. SmartEvent GUI
Answer: B
NEW QUESTION 18
Which statement is correct about the Sticky Decision Function?
- A. It is not supported with either the Performance pack of a hardware based accelerator card
- B. Does not support SPI’s when configured for Load Sharing
- C. It is automatically disabled if the Mobile Access Software Blade is enabled on the cluster
- D. It is not required L2TP traffic
Answer: A
NEW QUESTION 19
When deploying SandBlast, how would a Threat Emulation appliance benefit from the integration of ThreatCloud?
- A. ThreatCloud is a database-related application which is located on-premise to preserve privacy of company-related data
- B. ThreatCloud is a collaboration platform for all the CheckPoint customers to form a virtual cloud consisting of a combination of all on-premise private cloud environments
- C. ThreatCloud is a collaboration platform for Check Point customers to benefit from VMWare ESXi infrastructure which supports the Threat Emulation Appliances as virtual machines in the EMC Cloud
- D. ThreatCloud is a collaboration platform for all the Check Point customers to share information about malicious and benign files that all of the customers can benefit from as it makes emulation of known files unnecessary
Answer: D
NEW QUESTION 20
......
P.S. Easily pass 156-315.80 Exam with 428 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 156-315.80 Dumps: https://www.certleader.com/156-315.80-dumps.html (428 New Questions)