156-315.80 | A Review Of Pinpoint 156-315.80 Free Exam Questions
We provide real 156-315.80 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Check-Point 156-315.80 Exam quickly & easily. The 156-315.80 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Check-Point 156-315.80 dumps pdf and vce product and material, you can easily pass the 156-315.80 exam.
Check 156-315.80 free dumps before getting the full version:
NEW QUESTION 1
Which of the following is NOT a type of Endpoint Identity Agent?
- A. Terminal
- B. Light
- C. Full
- D. Custom
Answer: A
NEW QUESTION 2
To help SmartEvent determine whether events originated internally or externally you must define using the Initial Settings under General Settings in the Policy Tab. How many options are available to calculate the traffic direction?
- A. 5 Network; Host; Objects; Services; API
- B. 3 Incoming; Outgoing; Network
- C. 2 Internal; External
- D. 4 Incoming; Outgoing; Internal; Other
Answer: D
NEW QUESTION 3
Which is not a blade option when configuring SmartEvent?
- A. Correlation Unit
- B. SmartEvent Unit
- C. SmartEvent Server
- D. Log Server
Answer: B
Explanation:
On the Management tab, enable these Software Blades: References:
NEW QUESTION 4
Which command is used to display status information for various components?
- A. show all systems
- B. show system messages
- C. sysmess all
- D. show sysenv all
Answer: D
NEW QUESTION 5
What command would show the API server status?
- A. cpm status
- B. api restart
- C. api status
- D. show api status
Answer: C
NEW QUESTION 6
What is the name of the secure application for Mail/Calendar for mobile devices?
- A. Capsule Workspace
- B. Capsule Mail
- C. Capsule VPN
- D. Secure Workspace
Answer: A
NEW QUESTION 7
What are types of Check Point APIs available currently as part of R80.10 code?
- A. Security Gateway API Management API, Threat Prevention API and Identity Awareness Web Services API
- B. Management API, Threat Prevention API, Identity Awareness Web Services API and OPSEC SDK API
- C. OSE API, OPSEC SDK API, Threat Extraction API and Policy Editor API
- D. CPMI API, Management API, Threat Prevention API and Identity Awareness Web Services API
Answer: B
NEW QUESTION 8
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
- A. Install appliance TE250X on SpanPort on LAN switch in MTA mode.
- B. Install appliance TE250X in standalone mode and setup MTA.
- C. You can utilize only Check Point Cloud Services for this scenario.
- D. It is not possible, always Check Point SGW is needed to forward emails to SandBlast appliance.
Answer: C
NEW QUESTION 9
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated.
What is the most likely reason that the traffic is not accelerated?
- A. There is a virus foun
- B. Traffic is still allowed but not accelerated.
- C. The connection required a Security server.
- D. Acceleration is not enabled.
- E. The traffic is originating from the gateway itself.
Answer: D
NEW QUESTION 10
What processes does CPM control?
- A. Object-Store, Database changes, CPM Process and web-services
- B. web-services, CPMI process, DLEserver, CPM process
- C. DLEServer, Object-Store, CP Process and database changes
- D. web_services, dle_server and object_Store
Answer: D
NEW QUESTION 11
For Management High Availability, which of the following is NOT a valid synchronization status?
- A. Collision
- B. Down
- C. Lagging
- D. Never been synchronized
Answer: B
NEW QUESTION 12
The Security Gateway is installed on GAIA R80. The default port for the Web User Interface is ______.
- A. TCP 18211
- B. TCP 257
- C. TCP 4433
- D. TCP 443
Answer: D
NEW QUESTION 13
What are the three components for Check Point Capsule?
- A. Capsule Docs, Capsule Cloud, Capsule Connect
- B. Capsule Workspace, Capsule Cloud, Capsule Connect
- C. Capsule Workspace, Capsule Docs, Capsule Connect
- D. Capsule Workspace, Capsule Docs, Capsule Cloud
Answer: D
NEW QUESTION 14
SandBlast Mobile identifies threats in mobile devices by using on-device, network, and cloud-based algorithms and has four dedicated components that constantly work together to protect mobile devices and their data. Which component is NOT part of the SandBlast Mobile solution?
- A. Management Dashboard
- B. Gateway
- C. Personal User Storage
- D. Behavior Risk Engine
Answer: C
NEW QUESTION 15
Which statement is true regarding redundancy?
- A. System Administrators know when their cluster has failed over and can also see why it failed over by using the cphaprob –f if command.
- B. ClusterXL offers three different Load Sharing solutions: Unicast, Broadcast, and Multicast.
- C. Machines in a ClusterXL High Availability configuration must be synchronized.
- D. Both ClusterXL and VRRP are fully supported by Gaia and available to all Check Point appliances, open servers, and virtualized environments.
Answer: D
NEW QUESTION 16
CPM process stores objects, policies, users, administrators, licenses and management data in a database. The database is:
- A. MySQL
- B. Postgres SQL
- C. MarisDB
- D. SOLR
Answer: B
NEW QUESTION 17
What command can you use to have cpinfo display all installed hotfixes?
- A. cpinfo -hf
- B. cpinfo –y all
- C. cpinfo –get hf
- D. cpinfo installed_jumbo
Answer: B
NEW QUESTION 18
View the rule below. What does the lock-symbol in the left column mean? (Choose the BEST answer.)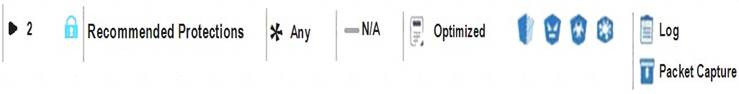
- A. The current administrator has read-only permissions to Threat Prevention Policy.
- B. Another user has locked the rule for editing.
- C. Configuration lock is presen
- D. Click the lock symbol to gain read-write access.
- E. The current administrator is logged in as read-only because someone else is editing the policy.
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_
NEW QUESTION 19
Hit Count is a feature to track the number of connections that each rule matches, which one is not benefit of Hit Count.
- A. Better understand the behavior of the Access Control Policy
- B. Improve Firewall performance - You can move a rule that has hot count to a higher position in the Rule Base
- C. Automatically rearrange Access Control Policy based on Hit Count Analysis
- D. Analyze a Rule Base - You can delete rules that have no matching connections
Answer: C
NEW QUESTION 20
......
P.S. Easily pass 156-315.80 Exam with 428 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com 156-315.80 Dumps: https://www.dumpscollection.net/dumps/156-315.80/ (428 New Questions)