212-89 | Pinpoint 212-89 Questions 2021
Exam Code: 212-89 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: EC Council Certified Incident Handler (ECIH v2)
Certification Provider: EC-Council
Free Today! Guaranteed Training- Pass 212-89 Exam.
EC-Council 212-89 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
In the Control Analysis stage of the NIST’s risk assessment methodology, technical and none technical control methods are classified into two categories. What are these two control categories?
- A. Preventive and Detective controls
- B. Detective and Disguised controls
- C. Predictive and Detective controls
- D. Preventive and predictive controls
Answer: A
NEW QUESTION 2
Incident handling and response steps help you to detect, identify, respond and manage an incident. Which of the following steps focus on limiting the scope and extent of an incident?
- A. Eradication
- B. Containment
- C. Identification
- D. Data collection
Answer: B
NEW QUESTION 3
A computer Risk Policy is a set of ideas to be implemented to overcome the risk associated with computer security incidents. Identify the procedure that is NOT part of the computer risk policy?
- A. Procedure to identify security funds to hedge risk
- B. Procedure to monitor the efficiency of security controls
- C. Procedure for the ongoing training of employees authorized to access the system
- D. Provisions for continuing support if there is an interruption in the system or if the system crashes
Answer: C
NEW QUESTION 4
Absorbing minor risks while preparing to respond to major ones is called:
- A. Risk Mitigation
- B. Risk Transfer
- C. Risk Assumption
- D. Risk Avoidance
Answer: C
NEW QUESTION 5
Which of the following is NOT one of the common techniques used to detect Insider threats:
- A. Spotting an increase in their performance
- B. Observing employee tardiness and unexplained absenteeism
- C. Observing employee sick leaves
- D. Spotting conflicts with supervisors and coworkers
Answer: A
NEW QUESTION 6
To recover, analyze, and preserve computer and related materials in such a way that it can be presented as evidence in a court of law and identify the evidence in short time, estimate the potential impact of the malicious activity on the victim, and assess the intent and identity of the perpetrator is known as:
- A. Computer Forensics
- B. Digital Forensic Analysis
- C. Forensic Readiness
- D. Digital Forensic Examiner
Answer: B
NEW QUESTION 7
Business Continuity planning includes other plans such as:
- A. Incident/disaster recovery plan
- B. Business recovery and resumption plans
- C. Contingency plan
- D. All the above
Answer: D
NEW QUESTION 8
Which of the following is an appropriate flow of the incident recovery steps?
- A. System Operation-System Restoration-System Validation-System Monitoring
- B. System Validation-System Operation-System Restoration-System Monitoring
- C. System Restoration-System Monitoring-System Validation-System Operations
- D. System Restoration-System Validation-System Operations-System Monitoring
Answer: D
NEW QUESTION 9
An access control policy authorized a group of users to perform a set of actions on a set of resources. Access to resources is based on necessity and if a particular job role requires the use of those resources. Which of the following is NOT a fundamental element of access control policy
- A. Action group: group of actions performed by the users on resources
- B. Development group: group of persons who develop the policy
- C. Resource group: resources controlled by the policy
- D. Access group: group of users to which the policy applies
Answer: B
NEW QUESTION 10
A Malicious code attack using emails is considered as:
- A. Malware based attack
- B. Email attack
- C. Inappropriate usage incident
- D. Multiple component attack
Answer: D
NEW QUESTION 11
When an employee is terminated from his or her job, what should be the next immediate step taken by an organization?
- A. All access rights of the employee to physical locations, networks, systems, applications and data should be disabled
- B. The organization should enforce separation of duties
- C. The access requests granted to an employee should be documented and vetted by the supervisor
- D. The organization should monitor the activities of the system administrators and privileged users who have permissions to access the sensitive information
Answer: A
NEW QUESTION 12
The correct order or sequence of the Computer Forensic processes is:
- A. Preparation, analysis, examination, collection, and reporting
- B. Preparation, collection, examination, analysis, and reporting
- C. Preparation, examination, collection, analysis, and reporting
- D. Preparation, analysis, collection, examination, and reporting
Answer: B
NEW QUESTION 13
What is correct about Quantitative Risk Analysis:
- A. It is Subjective but faster than Qualitative Risk Analysis
- B. Easily automated
- C. Better than Qualitative Risk Analysis
- D. Uses levels and descriptive expressions
Answer: B
NEW QUESTION 14
The sign of incident that may happen in the future is called:
- A. A Precursor
- B. An Indication
- C. A Proactive
- D. A Reactive
Answer: A
NEW QUESTION 15
Incident handling and response steps help you to detect, identify, respond and manage an incident. Which of the following helps in recognizing and separating the infected hosts from the information system?
- A. Configuring firewall to default settings
- B. Inspecting the process running on the system
- C. Browsing particular government websites
- D. Sending mails to only group of friends
Answer: B
NEW QUESTION 16
The role that applies appropriate technology and tries to eradicate and recover from the incident is known as:
- A. Incident Manager
- B. Incident Analyst
- C. Incident Handler
- D. Incident coordinator
Answer: B
NEW QUESTION 17
The flow chart gives a view of different roles played by the different personnel of CSIRT. Identify the incident response personnel denoted by A, B, C, D, E, F and G.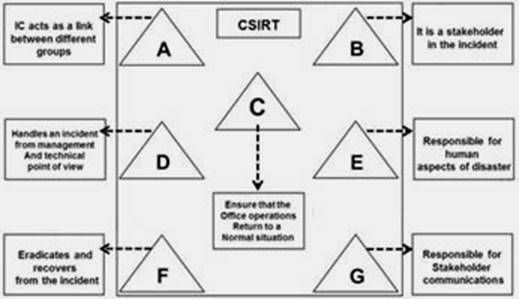
- A. A-Incident Analyst, B- Incident Coordinator, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Manager
- B. A- Incident Coordinator, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Manager
- C. A- Incident Coordinator, B- Constituency, C-Administrator, D-Incident Manager, E- Human Resource, FIncident Analyst, G-Public relations
- D. A- Incident Manager, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Coordinator
Answer: C
NEW QUESTION 18
An organization faced an information security incident where a disgruntled employee passed sensitive access control information to a competitor. The organization’s incident response manager, upon investigation, found that the incident must be handled within a few hours on the same day to maintain business continuity and market competitiveness. How would you categorize such information security incident?
- A. High level incident
- B. Middle level incident
- C. Ultra-High level incident
- D. Low level incident
Answer: A
NEW QUESTION 19
CSIRT can be implemented at:
- A. Internal enterprise level
- B. National, government and military level
- C. Vendor level
- D. All the above
Answer: D
NEW QUESTION 20
According to the Fourth Amendment of USA PATRIOT Act of 2001; if a search does NOT violate a person’s “reasonable” or “legitimate” expectation of privacy then it is considered:
- A. Constitutional/ Legitimate
- B. Illegal/ illegitimate
- C. Unethical
- D. None of the above
Answer: A
NEW QUESTION 21
Preventing the incident from spreading and limiting the scope of the incident is known as:
- A. Incident Eradication
- B. Incident Protection
- C. Incident Containment
- D. Incident Classification
Answer: C
NEW QUESTION 22
Which of the following is NOT a digital forensic analysis tool:
- A. Access Data FTK
- B. EAR/ Pilar
- C. Guidance Software EnCase Forensic
- D. Helix
Answer: B
NEW QUESTION 23
Policies are designed to protect the organizational resources on the network by establishing the set rules and procedures. Which of the following policies authorizes a group of users to perform a set of actions on a set of resources?
- A. Access control policy
- B. Audit trail policy
- C. Logging policy
- D. Documentation policy
Answer: A
NEW QUESTION 24
The IDS and IPS system logs indicating an unusual deviation from typical network traffic flows; this is called:
- A. A Precursor
- B. An Indication
- C. A Proactive
- D. A Reactive
Answer: B
NEW QUESTION 25
......
100% Valid and Newest Version 212-89 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/212-89/ (New 163 Q&As)