350-901 | All About Downloadable 350-901 Exam Engine
we provide Refined Cisco 350-901 book which are the best for clearing 350-901 test, and to get certified by Cisco Developing Applications using Cisco Core Platforms & APIs. The 350-901 Questions & Answers covers all the knowledge points of the real 350-901 exam. Crack your Cisco 350-901 Exam with latest dumps, guaranteed!
Cisco 350-901 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1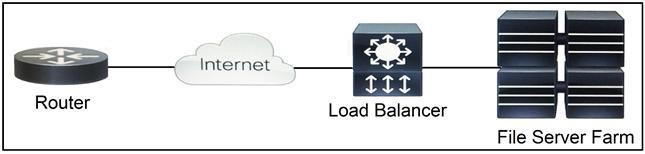
Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
- A. Terminate the TLS over the UDP connection from the router and originate an HTTPS connection to the selected server.
- B. Terminate the TLS over the UDP connection from the router and originate an HTTP connection to the selected server.
- C. Terminate the TLS over the TCP connection from the router and originate an HTTP connection to the selected server.
- D. Terminate the TLS over the TCP connection from the router and originate an HTTPS connection to the selected server.
- E. Terminate the TLS over the SCTP connection from the router and originate an HTTPS connection to the selected server.
Answer: DE
NEW QUESTION 2
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
- A. Update the base image of the containers.
- B. Test the execution of the application with another cloud services platform.
- C. Increase the number of containers running per service.
- D. Add consistent “try/catch(exception)” clauses to the code.
Answer: D
NEW QUESTION 3
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
- A. Store data in a NoSQL database.
- B. Implement message authentication (HMAC).
- C. Enable end-to-end encryption.
- D. Remove stack traces from errors.
- E. Use short-lived access tokens.
Answer: BE
NEW QUESTION 4
Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
- A.

- B.
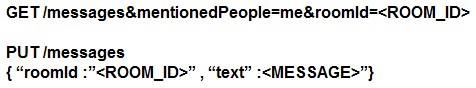
- C.
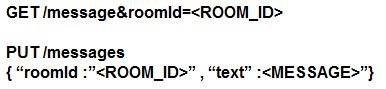
- D.
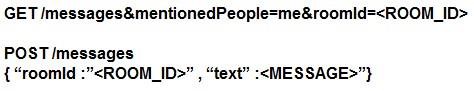
Answer: B
NEW QUESTION 5
Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
- A. environment variables
- B. YAML files
- C. Python libraries
- D. Dockerfiles
- E. INI files
Answer: B
NEW QUESTION 6
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
- A. Create a Dockerfile for the code base.
- B. Rewrite the code in Python.
- C. Build a wrapper for the code to “containerize” it.
- D. Rebase the code from the upstream git repo.
Answer: D
NEW QUESTION 7
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
- A. DER
- B. CSR
- C. PEM
- D. CRT
Answer: C
NEW QUESTION 8
Which two data encoding techniques are supported by gRPC? (Choose two.)
- A. XML
- B. JSON
- C. ASCII
- D. ProtoBuf
- E. YAML
Answer: BE
NEW QUESTION 9
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
- A. Embed them directly in the code.
- B. Store them in a hidden file.
- C. Store them inside the source tree of the application.
- D. Change them periodically.
Answer: D
NEW QUESTION 10
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
- A. Apply ip nat overload on VirtualPortGroup0.
- B. Apply ip nat inside on Interface VirtualPortGroup0.
- C. Apply ip nat outside on Interface VirtualPortGroup0.
- D. Apply ip nat inside on Interface GigabitEthernet1.
Answer: B
NEW QUESTION 11
A developer has completed the implementation of a REST API, but when it is executed, it returns a 401 error message. What must be done on the API to resolve the issue?
- A. Access permission to the resource must be granted, before the request.
- B. Configure new valid credentials.
- C. The requested API endpoint does not exist, and the request URL must be changed.
- D. Additional permission must be granted before the request can submitted.
Answer: D
NEW QUESTION 12
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
- A. It checks for potential tainted data where input is not checked.
- B. It enforces proper coding standards and style.
- C. It performs a quick analysis of whether tests will pass or fail when run.
- D. It checks for race conditions in threaded applications.
- E. It estimates the performance of the code when run.
Answer: BC
NEW QUESTION 13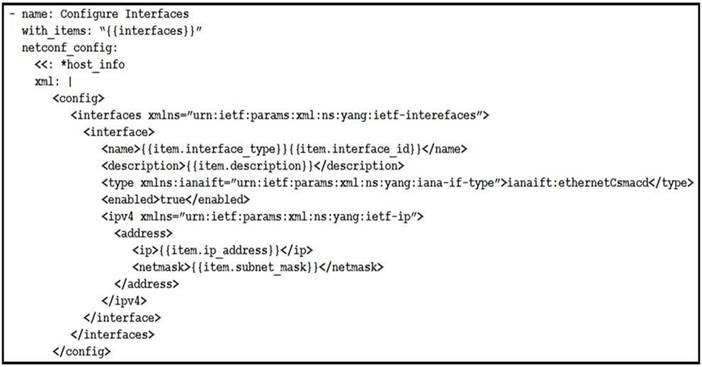
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
- A. ietf-interfaces and ietf-ip
- B. iana-if-type and ietf-interfaces
- C. ietf-ip and openconfig-interface
- D. ietf-ip and iana-if-type
Answer: B
NEW QUESTION 14
The response from a server includes the header ETag: W/”7eb8b94419e371767916ef13e0d6e63d”. Which statement is true?
- A. The ETag has a Strong validator directive.
- B. The ETag has a Weak validator directive, which is an optional directive.
- C. The ETag has a Weak validator directive, which is a mandatory directive.
- D. The ETag has a Strong validator directive, which it is incorrectly formatted.
Answer: B
NEW QUESTION 15
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScnpt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline.
Which step should be omitted from the pipeline?
- A. Deploy the code to one or more environments, such as staging and/or production.
- B. Build one of more containers that package up code and all its dependencies.
- C. Compile code.
- D. Run automated tests to validate the correctness.
Answer: A
NEW QUESTION 16
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
- A. An application is always tracked in a version control system.
- B. There are multiple codebases per application.
- C. The codebase is the same across all deploys.
- D. There can be a many-to-one correlation between codebase and application.
- E. It is only possible to have one application deployment per codebase.
Answer: AE
NEW QUESTION 17
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
- A. external USB storage
- B. internal SSD
- C. CD-ROM
- D. SD-card
- E. bootflash
Answer: AB
NEW QUESTION 18
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
- A. trunk interface
- B. bridged virtual interface
- C. SPAN port
- D. management interface
- E. subinterface
Answer: AC
NEW QUESTION 19
Which two methods are API security best practices? (Choose two.)
- A. Use tokens after the identity of a client has been established.
- B. Use the same operating system throughout the infrastructure.
- C. Use encryption and signatures to secure data.
- D. Use basic auth credentials over all internal API interactions.
- E. Use cloud hosting services to manage security configuration.
Answer: AC
NEW QUESTION 20
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
- A. Write a log to a file in the application directory.
- B. Write a log to a file in /var/log.
- C. Write the logs buffered to stdout.
- D. Write the logs unbuffered to stdout.
Answer: D
NEW QUESTION 21
DRAG DROP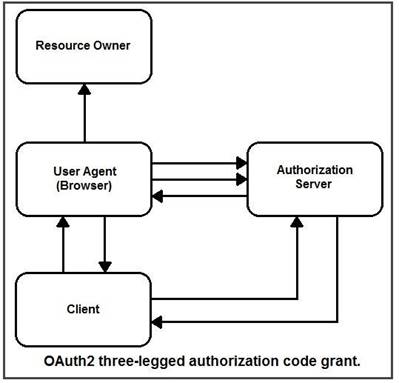
Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Select and Place: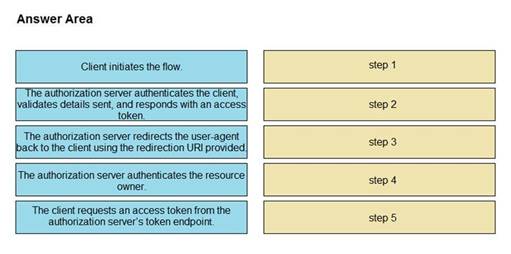
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 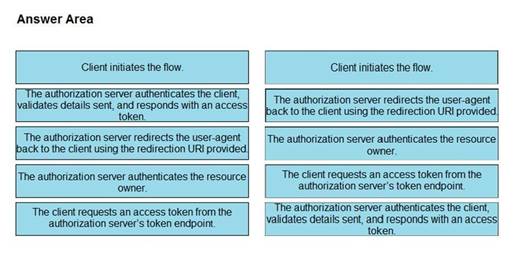
NEW QUESTION 22
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 23
Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
- A. This file is a container to log possible error responses in the request.
- B. This file is given as input to store the access token received from FDM.
- C. This file is used to send authentication related headers.
- D. This file contains raw data that is needed for token authentication.
Answer: B
NEW QUESTION 24
Which two techniques protect against injection attacks? (Choose two.)
- A. input validation
- B. trim whitespace
- C. limit text areas to 255 characters
- D. string escaping of user free text and data entry
- E. only use dropdown, checkbox, and radio button fields
Answer: AE
NEW QUESTION 25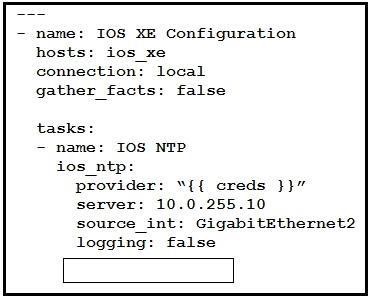
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
- A. state: present
- B. state: True
- C. config: present
- D. config: True
Answer: A
NEW QUESTION 26
......
P.S. Dumps-files.com now are offering 100% pass ensure 350-901 dumps! All 350-901 exam questions have been updated with correct answers: https://www.dumps-files.com/files/350-901/ (0 New Questions)