412-79v10 | A Review Of Breathing 412-79v10 Pdf Exam
100% Guarantee of 412-79v10 rapidshare materials and free dumps for EC-Council certification for consumer, Real Success Guaranteed with Updated 412-79v10 pdf dumps vce Materials. 100% PASS EC-Council Certified Security Analyst (ECSA) V10 exam Today!
Online EC-Council 412-79v10 free dumps demo Below:
NEW QUESTION 1
After attending a CEH security seminar, you make a list of changes you would like to perform on your
network to increase its security. One of the first things you change is to switch the Restrict Anonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server.
Using User info tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
- A. Restrict Anonymous must be set to "2" for complete security
- B. Restrict Anonymous must be set to "3" for complete security
- C. There is no way to always prevent an anonymous null session from establishing
- D. Restrict Anonymous must be set to "10" for complete security
Answer: A
NEW QUESTION 2
Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
include <stdio.h>
#include <string.h>
int main(int argc, char *argv[])
{
char buffer[10]; if (argc < 2)
{
fprintf(stderr, "USAGE: %s stringn", argv[0]); return 1;
}
strcpy(buffer, argv[1]); return 0;
}
- A. Buffer overflow
- B. Format string bug
- C. Kernal injection
- D. SQL injection
Answer: A
NEW QUESTION 3
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
- A. Phishing
- B. Spoofing
- C. Tapping
- D. Vishing
Answer: D
NEW QUESTION 4
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
- A. Connect Scanning Techniques
- B. SYN Scanning Techniques
- C. Stealth Scanning Techniques
- D. Port Scanning Techniques
Answer: C
NEW QUESTION 5
How many possible sequence number combinations are there in TCP/IP protocol?
- A. 320 billion
- B. 32 million
- C. 4 billion
- D. 1 billion
Answer: C
NEW QUESTION 6
A firewall’s decision to forward or reject traffic in network filtering is dependent upon which of the following?
- A. Destination address
- B. Port numbers
- C. Source address
- D. Protocol used
Answer: D
NEW QUESTION 7
What operating system would respond to the following command?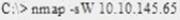
- A. Mac OS X
- B. Windows XP
- C. Windows 95
- D. FreeBSD
Answer: D
NEW QUESTION 8
Which of the following attacks does a hacker perform in order to obtain UDDI information such as businessEntity, businesService, bindingTemplate, and tModel?
- A. Web Services Footprinting Attack
- B. Service Level Configuration Attacks
- C. URL Tampering Attacks
- D. Inside Attacks
Answer: A
NEW QUESTION 9
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
- A. AES
- B. DES (ECB mode)
- C. MD5
- D. RC5
Answer: C
NEW QUESTION 10
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories.
Identify the attacks that fall under Passive attacks category.
- A. Wardriving
- B. Spoofing
- C. Sniffing
- D. Network Hijacking
Answer: A
NEW QUESTION 11
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer: A
NEW QUESTION 12
The objective of this act was to protect consumers personal financial information held by financial institutions and their service providers.
- A. HIPAA
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act
- D. California SB 1386a
Answer: C
NEW QUESTION 13
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
- A. Active/Passive Tools
- B. Application-layer Vulnerability Assessment Tools
- C. Location/Data Examined Tools
- D. Scope Assessment Tools
Answer: D
NEW QUESTION 14
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
- A. UDP and TCP
- B. TCP and SMTP
- C. SMTP
- D. UDP and SMTP
Answer: A
NEW QUESTION 15
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 16
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
- A. Localhost (127.0.0.1) and port 1241
- B. Localhost (127.0.0.1) and port 1240
- C. Localhost (127.0.0.1) and port 1246
- D. Localhost (127.0.0.0) and port 1243
Answer: A
NEW QUESTION 17
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
- A. Server Side Includes
- B. Sort Server Includes
- C. Server Sort Includes
- D. Slide Server Includes
Answer: A
NEW QUESTION 18
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive.org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code.
While searching through the code, you come across something abnormal:
<img
src=http://coolwebsearch.com/ads/pixel.news.com width=1 height=1 border=0
>
What have you found?
- A. Trojan.downloader
- B. Blind bug
- C. Web bug
- D. CGI code
Answer: C
NEW QUESTION 19
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.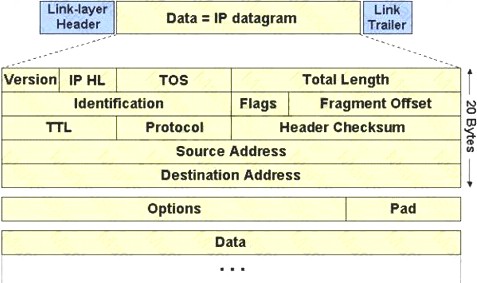
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer: C
NEW QUESTION 20
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
- A. Circuit-level proxy firewall
- B. Packet filtering firewall
- C. Application-level proxy firewall
- D. Statefull firewall
Answer: D
NEW QUESTION 21
......
Thanks for reading the newest 412-79v10 exam dumps! We recommend you to try the PREMIUM Allfreedumps.com 412-79v10 dumps in VCE and PDF here: https://www.allfreedumps.com/412-79v10-dumps.html (201 Q&As Dumps)