SY0-601 | Highest Quality CompTIA SY0-601 Exam Topics Online
We provide real SY0-601 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA SY0-601 Exam quickly & easily. The SY0-601 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA SY0-601 dumps pdf and vce product and material, you can easily pass the SY0-601 exam.
Free demo questions for CompTIA SY0-601 Exam Dumps Below:
NEW QUESTION 1
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
- A. A script kiddie
- B. Shadow IT
- C. Hacktivism
- D. White-hat
Answer: B
NEW QUESTION 2
A network engineer needs to create a plan for upgrading the wireless infrastructure in a large office Priority must be given to areas that are currently experiencing latency and connection issues. Which of the following would be the BEST resource for determining the order of priority?
- A. Nmapn
- B. Heat maps
- C. Network diagrams
- D. Wireshark
Answer: C
NEW QUESTION 3
An organization has hired a security analyst to perform a penetration test. The analyst captures 1Gb worth of inbound network traffic to the server and transfer the pcap back to the machine for analysis. Which of the following tools should the analyst use to further review the pcap?
- A. Nmap
- B. cURL
- C. Netcat
- D. Wireshark
Answer: D
NEW QUESTION 4
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which of the following methods would BEST prevent the exfiltration of data? (Select TWO).
- A. VPN
- B. Drive encryption
- C. Network firewall
- D. File level encryption
- E. USB blocker
- F. MFA
Answer: BE
NEW QUESTION 5
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output: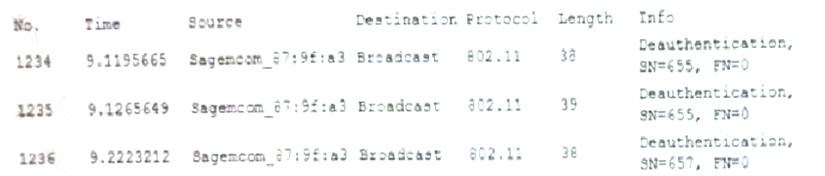
Which of the following attacks does the analyst MOST likely see in this packet capture?
- A. Session replay
- B. Evil twin
- C. Bluejacking
- D. ARP poisoning
Answer: B
NEW QUESTION 6
A security analyst is performing a forensic investigation compromised account credentials. Using the Event Viewer, the analyst able to detect the following message, ‘’Special privileges assigned to new login.’’ Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
- A. Pass-the-hash
- B. Buffer overflow
- C. Cross-site scripting
- D. Session replay
Answer: A
NEW QUESTION 7
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
- A. Network location
- B. Impossible travel time
- C. Geolocation
- D. Geofencing
Answer: D
NEW QUESTION 8
The Chief Executive Officer (CEO) of an organization would like staff members to have the flexibility to work from home anytime during business hours, incident during a pandemic or crisis, However, the CEO is concerned that some staff members may take advantage of the of the flexibility and work from high-risk countries while on holidays work to a third-party organization in another country. The Chief information Officer (CIO) believes the company can implement some basic to mitigate the majority of the risk. Which of the following would be BEST to mitigate CEO’s concern? (Select TWO).
- A. Geolocation
- B. Time-of-day restrictions
- C. Certificates
- D. Tokens
- E. Geotagging
- F. Role-based access controls
Answer: AE
NEW QUESTION 9
Which of the following algorithms has the SMALLEST key size?
- A. DES
- B. Twofish
- C. RSA
- D. AES
Answer: B
NEW QUESTION 10
Which of the following scenarios would make a DNS sinkhole effective in thwarting an attack?
- A. An attacker is sniffing traffic to port 53, and the server is managed using unencrypted usernames and passwords.
- B. An organization is experiencing excessive traffic on port 53 and suspects an attacker is trying to DoS the domain name server.
- C. Malware trying to resolve an unregistered domain name to determine if it is running in an isolated sandbox
- D. Routing tables have been compromised, and an attacker is rerouting traffic to malicious websites
Answer: A
NEW QUESTION 11
An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following: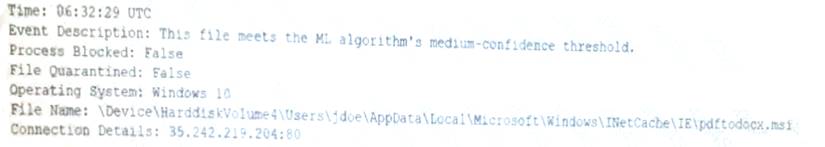
Which of the following is the MOST likely cause of the issue?
- A. The end user purchased and installed a PUP from a web browser
- B. A bot on the computer is brute forcing passwords against a website
- C. A hacker is attempting to exfiltrate sensitive data
- D. Ransomware is communicating with a command-and-control server.
Answer: A
NEW QUESTION 12
Which of the following would be BEST to establish between organizations that have agreed cooperate and are engaged in early discussion to define the responsibilities of each party, but do not want to establish a contractually binding agreement?
- A. An SLA
- B. AnNDA
- C. ABPA
- D. AnMOU
Answer: D
NEW QUESTION 13
A system administrator needs to implement an access control scheme that will allow an object’s access policy be determined by its owner. Which of the following access control schemes BEST fits the requirements?
- A. Role-based access control
- B. Discretionary access control
- C. Mandatory access control
- D. Attribute-based access control
Answer: B
NEW QUESTION 14
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two- drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
- A. 1
- B. 5
- C. 6
Answer: B
NEW QUESTION 15
A cybersecurity analyst needs to implement secure authentication to third-party websites without users’ passwords. Which of the following would be the BEST way to achieve this objective?
- A. OAuth
- B. SSO
- C. SAML
- D. PAP
Answer: C
NEW QUESTION 16
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
- A. Something you know
- B. Something you have
- C. Somewhere you are
- D. Someone you are
- E. Something you are
- F. Something you can do
Answer: BE
NEW QUESTION 17
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
- A. SSAE SOC 2
- B. PCI DSS
- C. GDPR
- D. ISO 31000
Answer: C
NEW QUESTION 18
A software developer needs to perform code-execution testing, black-box testing, and non-functional testing on a new product before its general release. Which of the following BEST describes the tasks the developer is conducting?
- A. Verification
- B. Validation
- C. Normalization
- D. Staging
Answer: A
NEW QUESTION 19
A security analyst sees the following log output while reviewing web logs:
Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
- A. Secure cookies
- B. Input validation
- C. Code signing
- D. Stored procedures
Answer: B
NEW QUESTION 20
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
- A. PCI DSS
- B. ISO 22301
- C. ISO 27001
- D. NIST CSF
Answer: A
NEW QUESTION 21
A website developer is working on a new e-commerce website and has asked an information security expert for the most appropriate way to store credit card numbers to create an easy reordering process. Which of the following methods would BEST accomplish this goal?
- A. Salting the magnetic strip information
- B. Encrypting the credit card information in transit.
- C. Hashing the credit card numbers upon entry.
- D. Tokenizing the credit cards in the database
Answer: C
NEW QUESTION 22
A small company that does not have security staff wants to improve its security posture. Which of the following would BEST assist the company?
- A. MSSP
- B. SOAR
- C. IaaS
- D. PaaS
Answer: B
NEW QUESTION 23
......
P.S. Easily pass SY0-601 Exam with 218 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader SY0-601 Dumps: https://www.certleader.com/SY0-601-dumps.html (218 New Questions)