156-215.77 | Check Point 156-215.77 Free Practice Questions 2021
It is more faster and easier to pass the 156 215.77 pdf by using ccsa 156 215.77. Immediate access to the checkpoint 156 215.77 and find the same core area exam 156 215.77 with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Check Point 156-215.77 Exam Dumps Below:
NEW QUESTION 1
The Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). What is not a recommended usage of this method?
- A. When accuracy in detecting identity is crucial
- B. Leveraging identity for Data Center protection
- C. Protecting highly sensitive servers
- D. Identity based enforcement for non-AD users (non-Windows and guest users)
Answer: D
NEW QUESTION 2
Which of the following are authentication methods that Security Gateway R77 uses to validate connection attempts? Select the response below that includes the MOST complete list of valid authentication methods.
- A. Proxied, User, Dynamic, Session
- B. Connection, User, Client
- C. User, Client, Session
- D. User, Proxied, Session
Answer: C
NEW QUESTION 3
Where does the security administrator activate Identity Awareness within SmartDashboard?
- A. Gateway Object > General Properties
- B. Security Management Server > Identity Awareness
- C. Policy > Global Properties > Identity Awareness
- D. LDAP Server Object > General Properties
Answer: A
NEW QUESTION 4
You need to completely reboot the Operating System after making which of the following changes on the Security Gateway? (i.e. the command cprestart is not sufficient.)
1. Adding a hot-swappable NIC to the Operating System for the first time.
2. Uninstalling the R77 Power/UTM package.
3. Installing the R77 Power/UTM package.
4. Re-establishing SIC to the Security Management Server.
5. Doubling the maximum number of connections accepted by the Security Gateway.
- A. 3 only
- B. 1, 2, 3, 4, and 5
- C. 2, 3 only
- D. 3, 4, and 5 only
Answer: C
NEW QUESTION 5
You install and deploy GAiA with default settings. You allow Visitor Mode in the Gateway object’s Remote Access properties and install policy. What additional steps are required for this to function correctly?
- A. You need to start SSL Network Extender first, then use Visitor Mode.
- B. Set Visitor Mode in Policy > Global Properties > Remote-Access > VPN - Advanced.
- C. Office mode is not configured.
- D. The WebUI on GAiA runs on port 443 (HTTPS). When you configure Visitor Mode it cannot bind to default port 443, because it's used by another program (WebUI). With multi- port no additional changes are necessary.
Answer: D
NEW QUESTION 6
Which SmartView Tracker selection would most effectively show who installed a Security Policy blocking all traffic from the corporate network?
- A. Management tab
- B. Custom filter
- C. Network and Endpoint tab
- D. Active tab
Answer: A
NEW QUESTION 7
How do you configure the Security Policy to provide user access to the Captive Portal through an external (Internet) interface?
- A. Change the gateway settings to allow Captive Portal access via an external interface.
- B. No action is necessar
- C. This access is available by default.
- D. Change the Identity Awareness settings under Global Properties to allow Captive Portal access on all interfaces.
- E. Change the Identity Awareness settings under Global Properties to allow Captive Portal access for an external interface.
Answer: A
NEW QUESTION 8
When using LDAP as an authentication method for Identity Awareness, the query:
- A. Requires client and server side software.
- B. Prompts the user to enter credentials.
- C. Requires administrators to specifically allow LDAP traffic to and from the LDAP Server and the Security Gateway.
- D. Is transparent, requiring no client or server side software, or client intervention.
Answer: D
NEW QUESTION 9
Which of the following is true of a Stealth Rule?
- A. The Stealth rule should not be logged
- B. The Stealth rule is required for proper firewall protection
- C. The Stealth rule should be located just before the Cleanup rule
- D. The Stealth rule must be the first rule in a policy
Answer: B
NEW QUESTION 10
Your Security Management Server fails and does not reboot. One of your remote Security Gateways managed by the Security Management Server reboots.
What occurs with the remote Gateway after reboot?
- A. Since the Security Management Server is not available, the remote Gateway cannotfetch the Security Polic
- B. Therefore, all traffic is allowed through the Gateway.
- C. Since the Security Management Server is not available, the remote Gateway cannot fetch the Security Polic
- D. Therefore, no traffic is allowed through the Gateway.
- E. The remote Gateway fetches the last installed Security Policy locally and passes traffic normall
- F. The Gateway will log locally, since the Security Management Server is not available.
- G. Since the Security Management Server is not available, the remote Gateway uses the local Security Policy, but does not log traffic.
Answer: C
NEW QUESTION 11
Which of the following actions do NOT take place in IKE Phase 1?
- A. Peers agree on encryption method.
- B. Diffie-Hellman key is combined with the key material to produce the symmetrical IPsec key.
- C. Peers agree on integrity method.
- D. Each side generates a session key from its private key and the peer’s public key.
Answer: B
NEW QUESTION 12
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
- A. cpstat fwd
- B. fw ver
- C. fw stat
- D. fw ctl pstat
Answer: C
NEW QUESTION 13
Where do we need to reset the SIC on a gateway object?
- A. SmartDashboard > Edit Gateway Object > General Properties > Communication
- B. SmartUpdate > Edit Security Management Server Object > SIC
- C. SmartUpdate > Edit Gateway Object > Communication
- D. SmartDashboard > Edit Security Management Server Object > SIC
Answer: D
NEW QUESTION 14
What happens if the identity of a user is known?
- A. If the user credentials do not match an Access Role, the system displays the Captive Portal.
- B. If the user credentials do not match an Access Role, the system displays a sandbox.
- C. If the user credentials do not match an Access Role, the traffic is automatically dropped.
- D. If the user credentials match an Access Role, the rule is applied and traffic is accepted or dropped based on the defined action.
Answer: D
NEW QUESTION 15
Match the following commands to their correct function. Each command has one function only listed.
Exhibit: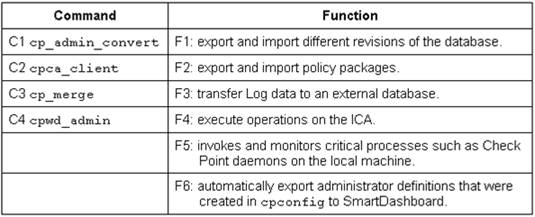
- A. C1>F6; C2>F4; C3>F2; C4>F5
- B. C1>F2; C2>F1; C3>F6; C4>F4
- C. C1>F2; C2>F4; C3>F1; C4>F5
- D. C1>F4; C2>F6; C3>F3; C4>F2
Answer: A
NEW QUESTION 16
Identity Awareness is implemented to manage access to protected resources based on a user’s .
- A. Application requirement
- B. Computer MAC address
- C. Identity
- D. Time of connection
Answer: C
NEW QUESTION 17
Which R77 GUI would you use to see the number of packets accepted since the last policy install?
- A. SmartView Monitor
- B. SmartView Tracker
- C. SmartDashboard
- D. SmartView Status
Answer: A
Recommend!! Get the Full 156-215.77 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/156-215.77-dumps.html (New 388 Q&As Version)