412-79v9 | The Secret Of EC-Council 412-79v9 Exams
Our pass rate is high to 98.9% and the similarity percentage between our 412-79v9 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the EC-Council 412-79v9 exam in just one try? I am currently studying for the EC-Council 412-79v9 exam. Latest EC-Council 412-79v9 Test exam practice questions and answers, Try EC-Council 412-79v9 Brain Dumps First.
Free 412-79v9 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
Traffic on which port is unusual for both the TCP and UDP ports?
- A. Port 81
- B. Port 443
- C. Port 0
- D. Port21
Answer: C
NEW QUESTION 2
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer: A
NEW QUESTION 3
Which of the following methods is used to perform server discovery?
- A. Banner Grabbing
- B. Whois Lookup
- C. SQL Injection
- D. Session Hijacking
Answer: B
Explanation:
Reference: http://luizfirmino.blogspot.com/2011/09/server-discovery.html
NEW QUESTION 4
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.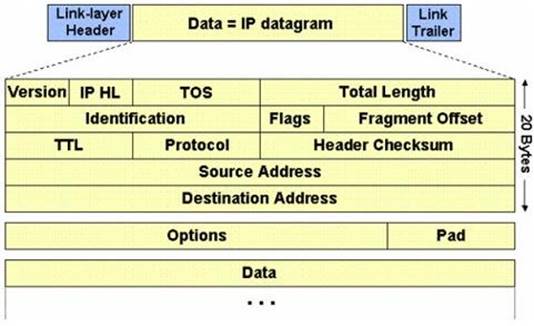
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer: C
Explanation:
Reference: http://www.freesoft.org/CIE/Course/Section3/7.htm (fragment offset: 13 bits)
NEW QUESTION 5
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 6
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
- A. Disgruntled employees
- B. Weaknesses that could be exploited
- C. Physical security breaches
- D. Organizational structure
Answer: B
NEW QUESTION 7
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.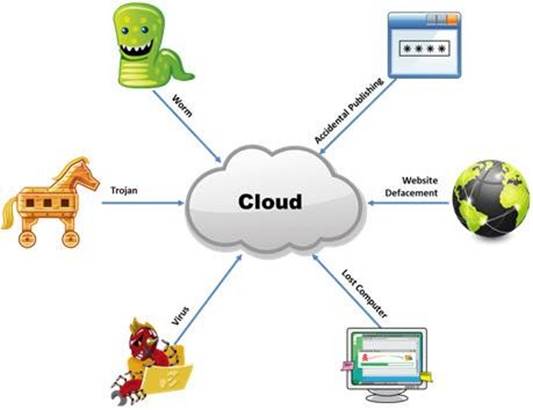
What is the biggest source of data leaks in organizations today?
- A. Weak passwords and lack of identity management
- B. Insufficient IT security budget
- C. Rogue employees and insider attacks
- D. Vulnerabilities, risks, and threats facing Web sites
Answer: C
NEW QUESTION 8
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using Idp.exe. What are you trying to accomplish here?
- A. Poison the DNS records with false records
- B. Enumerate MX and A records from DNS
- C. Establish a remote connection to the Domain Controller
- D. Enumerate domain user accounts and built-in groups
Answer: D
NEW QUESTION 9
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing. Management decide to block all such web sites using URL filtering software.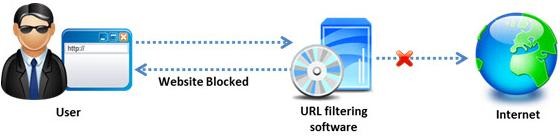
How can employees continue to see the blocked websites?
- A. Using session hijacking
- B. Using proxy servers
- C. Using authentication
- D. Using encryption
Answer: B
NEW QUESTION 10
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table:
http://juggyboy.com/page.aspx?id=1; IF (LEN(SELECT TOP 1 NAME from sysobjects where xtype='U')=3) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY '00:00:10'—
What is the table name?
- A. CTS
- B. QRT
- C. EMP
- D. ABC
Answer: C
NEW QUESTION 11
Identify the port numbers used by POP3 and POP3S protocols.
- A. 113 and 981
- B. 111 and 982
- C. 110 and 995
- D. 109 and 973
Answer: C
Explanation:
Reference: https://publib.boulder.ibm.com/infocenter/wsmashin/v1r1/index.jsp?topic=/com.ibm.websph ere.sMash.doc/using/zero.mail/MailStoreConfiguration.html
NEW QUESTION 12
Software firewalls work at which layer of the OSI model?
- A. Data Link
- B. Network
- C. Transport
- D. Application
Answer: A
NEW QUESTION 13
Which of the following statement holds true for TCP Operation?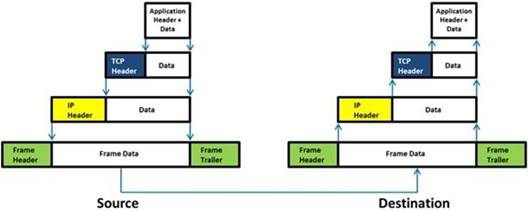
- A. Port numbers are used to know which application the receiving host should pass the data to
- B. Sequence numbers are used to track the number of packets lost in transmission
- C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
- D. Data transfer begins even before the connection is established
Answer: D
NEW QUESTION 14
Which one of the following 802.11 types has WLAN as a network support?
- A. 802.11b
- B. 802.11-Legacy
- C. 802.11n
- D. 802.11g
Answer: C
NEW QUESTION 15
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 16
Identify the type of firewall represented in the diagram below: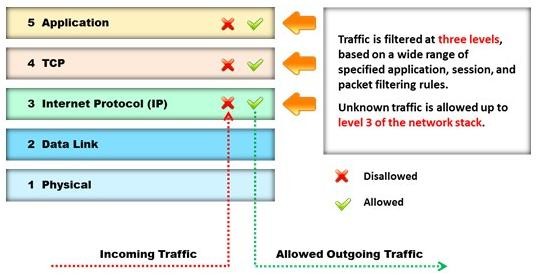
- A. Stateful multilayer inspection firewall
- B. Application level gateway
- C. Packet filter
- D. Circuit level gateway
Answer: A
Explanation:
Reference: http://www.technicolorbroadbandpartner.com/getfile.php?id=4159 (page 13)
NEW QUESTION 17
A penetration tester performs OS fingerprinting on the target server to identify the operating system used on the target server with the help of ICMP packets.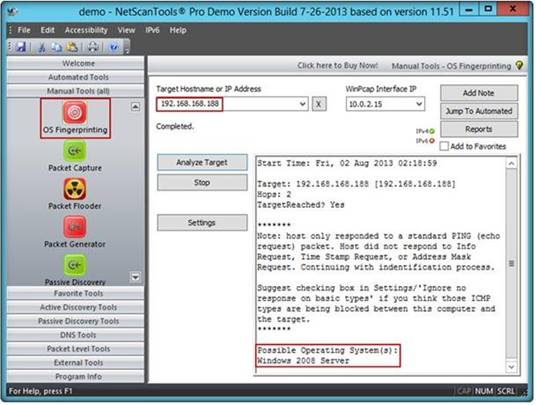
While performing ICMP scanning using Nmap tool, message received/type displays “3 – Destination Unreachable[5]” and code 3.
Which of the following is an appropriate description of this response?
- A. Destination port unreachable
- B. Destination host unavailable
- C. Destination host unreachable
- D. Destination protocol unreachable
Answer: A
NEW QUESTION 18
Security auditors determine the use of WAPs on their networks with Nessus vulnerability scanner which identifies the commonly used WAPs. One of the plug-ins that the Nessus Vulnerability Scanner uses is ID #11026 and is named “Access Point Detection”. This plug- in uses four techniques to identify the presence of a WAP. Which one of the following techniques is mostly used for uploading new firmware images while upgrading the WAP device?
- A. NMAP TCP/IP fingerprinting
- B. HTTP fingerprinting
- C. FTP fingerprinting
- D. SNMP fingerprinting
Answer: C
NEW QUESTION 19
A chipset is a group of integrated circuits that are designed to work together and are usually marketed as a single product.” It is generally the motherboard chips or the chips used on the expansion card. Which one of the following is well supported in most wireless applications?
- A. Orinoco chipsets
- B. Prism II chipsets
- C. Atheros Chipset
- D. Cisco chipset
Answer: B
NEW QUESTION 20
Identify the injection attack represented in the diagram below: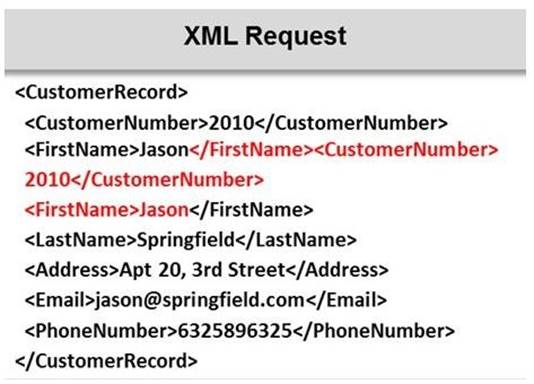
- A. XPath Injection Attack
- B. XML Request Attack
- C. XML Injection Attack
- D. Frame Injection Attack
Answer: C
Explanation:
Reference: http://projects.webappsec.org/w/page/13247004/XML%20Injection
NEW QUESTION 21
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top- level guidance for conducting the penetration testing.
Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.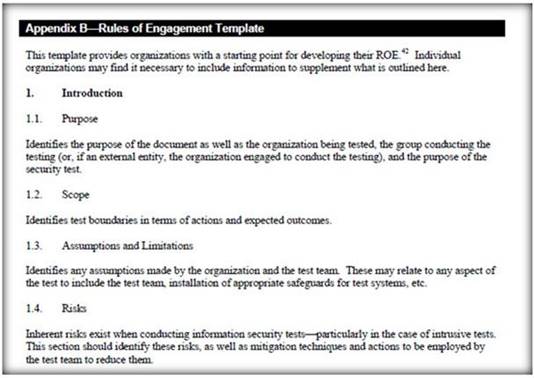
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
- A. A list of employees in the client organization
- B. A list of acceptable testing techniques
- C. Specific IP addresses/ranges to be tested
- D. Points of contact for the penetration testing team
Answer: A
NEW QUESTION 22
What is a goal of the penetration testing report?
- A. The penetration testing report helps you comply with local laws and regulations related to environmental conditions in the organization.
- B. The penetration testing report allows you to sleep better at night thinking your organization is protected
- C. The pen testing report helps executive management to make decisions on implementing security controls in the organization and helps the security team implement securitycontrols and patch any flaws discovered during testing.
- D. The penetration testing report allows you to increase sales performance by effectively communicating with the internal security team.
Answer: C
NEW QUESTION 23
Which one of the following scans starts, but does not complete the TCP handshake sequence for each port selected, and it works well for direct scanning and often works well through firewalls?
- A. SYN Scan
- B. Connect() scan
- C. XMAS Scan
- D. Null Scan
Answer: A
NEW QUESTION 24
The amount of data stored in organizational databases has increased rapidly in recent years due to the rapid advancement of information technologies. A high percentage of these data is sensitive, private and critical to the organizations, their clients and partners.
Therefore, databases are usually installed behind internal firewalls, protected with intrusion detection mechanisms and accessed only by applications. To access a database, users have to connect to one of these applications and submit queries through them to the database. The threat to databases arises when these applications do not behave properly and construct these queries without sanitizing user inputs first.
Identify the injection attack represented in the diagram below: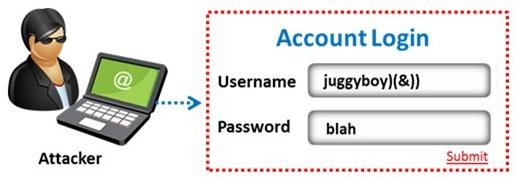
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: B
Explanation:
Reference: e https://www.blackhat.com/presentations/bh-europe-08/Alonso-Parada/Whitepaper/bh-eu-08-alonso-parada-WP.pdf ( page 3 to 5)
NEW QUESTION 25
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.
Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
- A. Total number of employees in the client organization
- B. Type of testers involved
- C. The budget required
- D. Expected time required to finish the project
Answer: A
NEW QUESTION 26
During the process of fingerprinting a web application environment, what do you need to do in order to analyze HTTP and HTTPS request headers and the HTML source code?
- A. Examine Source of the Available Pages
- B. Perform Web Spidering
- C. Perform Banner Grabbing
- D. Check the HTTP and HTML Processing by the Browser
Answer: D
NEW QUESTION 27
Identify the type of authentication mechanism represented below: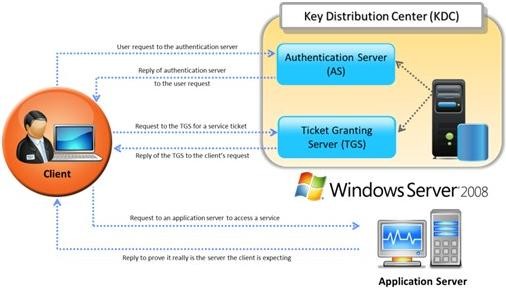
- A. NTLMv1
- B. NTLMv2
- C. LAN Manager Hash
- D. Kerberos
Answer: D
Explanation:
The client authenticates itself to the Authentication Server (AS) which forwards the username to a key distribution center (KDC). The KDC issues a ticket granting ticket (TGT), which is time stamped, encrypts it using the user's password and returns the encrypted result to the user's workstation. This is done infrequently, typically at user logon; the TGT expires at some point, though may be transparently renewed by the user's session manager while they are logged in.
When the client needs to communicate with another node ("principal" in Kerberos parlance) the client sends the TGT to the ticket granting service (TGS), which usually shares the same host as the KDC. After verifying the TGT is valid and the user is permitted to access the requested service, the TGS issues a ticket and session keys, which are returned to the client. The client then sends the ticket to the service server (SS) along with its service request.
Reference: http://en.wikipedia.org/wiki/Kerberos_(protocol)
NEW QUESTION 28
Which of the following equipment could a pen tester use to perform shoulder surfing?
- A. Binoculars
- B. Painted ultraviolet material
- C. Microphone
- D. All the above
Answer: A
Explanation:
Reference: http://en.wikipedia.org/wiki/Shoulder_surfing_(computer_security)
NEW QUESTION 29
During external penetration testing, which of the following techniques uses tools like Nmap to predict the sequence numbers generated by the targeted server and use this information to perform session hijacking techniques?
- A. TCP Sequence Number Prediction
- B. IPID State Number Prediction
- C. TCP State Number Prediction
- D. IPID Sequence Number Prediction
Answer: A
Explanation:
Reference: http://www.scribd.com/doc/133636402/LPTv4-Module-18-External-Penetration-Testing-NoRestriction (p.43)
NEW QUESTION 30
......
100% Valid and Newest Version 412-79v9 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/412-79v9-exam-dumps.html (New 203 Q&As)