CS0-002 | A Review Of Guaranteed CS0-002 Preparation Labs
Exam Code: CS0-002 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: CompTIA Cybersecurity Analyst (CySA+) Certification Exam
Certification Provider: CompTIA
Free Today! Guaranteed Training- Pass CS0-002 Exam.
Check CS0-002 free dumps before getting the full version:
NEW QUESTION 1
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period:
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and.
- A. DST 138.10.2.5.
- B. DST 138.10.25.5.
- C. DST 172.10.3.5.
- D. DST 172.10.45.5.
- E. DST 175.35.20.5.
Answer: A
NEW QUESTION 2
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.
Given the output, which of the following should the security analyst check NEXT?
- A. The DNS name of the new email server
- B. The version of SPF that is being used
- C. The IP address of the new email server
- D. The DMARC policy
Answer: B
NEW QUESTION 3
A cyber-incident response analyst is investigating a suspected cryptocurrency miner on a company's server. Which of the following is the FIRST step the analyst should take?
- A. Create a full disk image of the server's hard drive to look for the file containing the malware.
- B. Run a manual antivirus scan on the machine to look for known malicious software.
- C. Take a memory snapshot of the machine to capture volatile information stored in memory.
- D. Start packet capturing to look for traffic that could be indicative of command and control from the miner.
Answer: D
NEW QUESTION 4
Which of the following is the use of tools to simulate the ability for an attacker to gain access to a specified network?
- A. Reverse engineering
- B. Fuzzing
- C. Penetration testing
- D. Network mapping
Answer: C
NEW QUESTION 5
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Bing Data sets. Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
- A. $75.000
- B. $300.000
- C. $1.425 million
- D. $1.5 million
Answer: A
NEW QUESTION 6
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders Which of the following controls is the MOST appropriate to mitigate risks?
- A. Data deduplication
- B. OS fingerprinting
- C. Digital watermarking
- D. Data loss prevention
Answer: D
NEW QUESTION 7
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation platform.
Which of the following is MOST likely an attack vector that is being utilized as part of the testing and assessment?
- A. FaaS
- B. RTOS
- C. SoC
- D. GPS
- E. CAN bus
Answer: E
NEW QUESTION 8
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month, the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
- A. Deploy a WAF in front of the application.
- B. Implement a software repository management tool.
- C. Install a HIPS on the server.
- D. Instruct the developers to use input validation in the code.
Answer: B
NEW QUESTION 9
A web-based front end for a business intelligence application uses pass-through authentication to authenticate users The application then uses a service account, to perform queries and look up data m a database A security analyst discovers employees are accessing data sets they have not been authorized to use. Which of the following will fix the cause of the issue?
- A. Change the security model to force the users to access the database as themselves
- B. Parameterize queries to prevent unauthorized SQL queries against the database
- C. Configure database security logging using syslog or a SIEM
- D. Enforce unique session IDs so users do not get a reused session ID
Answer: B
NEW QUESTION 10
A cybersecurity analyst is contributing to a team hunt on an organization's endpoints. Which of the following should the analyst do FIRST?
- A. Write detection logic.
- B. Establish a hypothesis.
- C. Profile the threat actors and activities.
- D. Perform a process analysis.
Answer: C
NEW QUESTION 11
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains Management at an organization wants to know if it is a victim Which of the following should the security analyst recommend to identity this behavior without alerting any potential malicious actors?
- A. Create an IPS rule to block these domains and trigger an alert within the SIEM tool when these domains are requested
- B. Add the domains to a DNS sinkhole and create an alert m the SIEM toot when the domains are queried
- C. Look up the IP addresses for these domains and search firewall logs for any traffic being sent to those IPs over port 443
- D. Query DNS logs with a SIEM tool for any hosts requesting the malicious domains and create alerts based on this information
Answer: D
NEW QUESTION 12
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
- A. Add TXT @ "v=spf1 mx include:_spf.comptia.org all" to the DNS record.
- B. Add TXT @ "v=spf1 mx include:_spf.comptia.org all" to the email server.
- C. Add TXT @ "v=spf1 mx include:_spf.comptia.org +all" to the domain controller.
- D. Add TXT @ "v=spf1 mx include:_spf.comptia.org +all" to the web server.
Answer: A
NEW QUESTION 13
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient outside the organization The employee intended to send the spreadsheet to an internal staff member with a similar name and was unaware of the mistake until the recipient replied to the message In addition to retraining the employee, which of the following would prevent this from happening in the future?
- A. Implement outgoing filter rules to quarantine messages that contain card data
- B. Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
- C. Remove all external recipients from the employee's address book
- D. Set the outgoing mail filter to strip spreadsheet attachments from all messages.
Answer: B
NEW QUESTION 14
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful authentication, the user is then redirected back to the original page. Some users have reported receiving phishing emails with a link that takes them to the application login page but then redirects to a fake login page after successful authentication.
Which of the following will remediate this software vulnerability?
- A. Enforce unique session IDs for the application.
- B. Deploy a WAF in front of the web application.
- C. Check for and enforce the proper domain for the redirect.
- D. Use a parameterized query to check the credentials.
- E. Implement email filtering with anti-phishing protection.
Answer: D
NEW QUESTION 15
A security analyst is reviewing the following log from an email security service.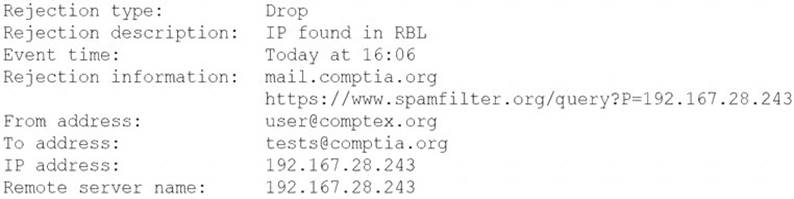
Which of the following BEST describes the reason why the email was blocked?
- A. The To address is invalid.
- B. The email originated from the www.spamfilter.org URL.
- C. The IP address and the remote server name are the same.
- D. The IP address was blacklisted.
- E. The From address is invalid.
Answer: D
NEW QUESTION 16
Which of the following are components of the intelligence cycle? (Select TWO.)
- A. Collection
- B. Normalization
- C. Response
- D. Analysis
- E. Correction
- F. Dissension
Answer: BE
NEW QUESTION 17
Which of the following will allow different cloud instances to share various types of data with a minimal amount of complexity?
- A. Reverse engineering
- B. Application log collectors
- C. Workflow orchestration
- D. API integration
- E. Scripting
Answer: D
NEW QUESTION 18
During an investigation, an incident responder intends to recover multiple pieces of digital media. Before removing the media, the responder should initiate:
- A. malware scans.
- B. secure communications.
- C. chain of custody forms.
- D. decryption tools.
Answer: C
NEW QUESTION 19
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website.
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
- A. An IPS signature modification for the specific IP addresses
- B. An IDS signature modification for the specific IP addresses
- C. A firewall rule that will block port 80 traffic
- D. A firewall rule that will block traffic from the specific IP addresses
Answer: D
NEW QUESTION 20
......
Thanks for reading the newest CS0-002 exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com CS0-002 dumps in VCE and PDF here: https://www.thedumpscentre.com/CS0-002-dumps/ (220 Q&As Dumps)