PT0-001 | A Review Of 100% Guarantee PT0-001 Free Question
Proper study guides for Rebirth CompTIA CompTIA PenTest+ Certification Exam certified begins with CompTIA PT0-001 preparation products which designed to deliver the Practical PT0-001 questions by making you pass the PT0-001 test at your first time. Try the free PT0-001 demo right now.
Online CompTIA PT0-001 free dumps demo Below:
NEW QUESTION 1
A penetration tester is designing a phishing campaign and wants to build list of users (or the target organization. Which of the following techniques would be the MOST appropriate? (Select TWO)
- A. Query an Internet WHOIS database.
- B. Search posted job listings.
- C. Scrape the company website.
- D. Harvest users from social networking sites.
- E. Socially engineer the corporate call cente
Answer: AB
NEW QUESTION 2
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
- A. dsrm -users "DN=compony.com; OU=hq CN=usera"
- B. dsuser -name -account -limit 3
- C. dsquery uaer -inactive 3
- D. dsquery -o -rein -limit 21
Answer: B
NEW QUESTION 3
A penetration tester successfully explogts a DM2 server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use few this purpose? (Select TWO)
- A. Tcpdump
- B. Nmap
- C. Wiresrtark
- D. SSH
- E. Netcat
- F. Cain and Abel
Answer: CD
NEW QUESTION 4
Which of the following types of physical security attacks does a mantrap mitigate-?
- A. Lock picking
- B. Impersonation
- C. Shoulder surfing
- D. Tailgating
Answer: D
NEW QUESTION 5
Which of the following reasons does penetration tester needs to have a customer's point-of -contact information available at all time? (Select THREE).
- A. To report indicators of compromise
- B. To report findings that cannot be explogted
- C. To report critical findings
- D. To report the latest published explogts
- E. To update payment information
- F. To report a server that becomes unresponsive
- G. To update the statement o( work
- H. To report a cracked password
Answer: DEF
NEW QUESTION 6
Which of the following would be BEST for performing passive reconnaissance on a target's external domain?
- A. Peach
- B. CeWL
- C. OpenVAS
- D. Shodan
Answer: A
NEW QUESTION 7
A client requests that a penetration tester emulate a help desk technician who was recently laid off. Which of the following BEST describes the abilities of the threat actor?
- A. Advanced persistent threat
- B. Script kiddie
- C. Hacktivist
- D. Organized crime
Answer: A
NEW QUESTION 8
Which of Ihe following commands would allow a penetration tester to access a private network from the Internet in Metasplogt?
- A. set rhost 192.168.1.10
- B. run autoroute -a 192.168.1.0/24
- C. db_nm«p -iL /tmp/privatehoots . txt
- D. use auxiliary/servet/aocka^a
Answer: D
NEW QUESTION 9
Given the following Python script: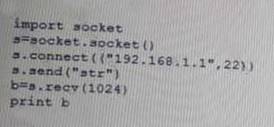
Which of the following actions will it perform?
- A. ARP spoofing
- B. Port scanner
- C. Reverse shell
- D. Banner grabbing
Answer: A
NEW QUESTION 10
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would defined the target list?
- A. Rules of engagement
- B. Master services agreement
- C. Statement of work
- D. End-user license agreement
Answer: D
NEW QUESTION 11
A penetration test was performed by an on-staff technicians junior technician. During the test, the technician discovered the application could disclose an SQL table with user account and password information. Which of the following is the MOST effective way to notify management of this finding and its importance?
- A. Document Ihe findtngs with an executive summary, recommendations, and screenshots of the web apphcation disclosure.
- B. Connect to the SQL server using this information and change the password to one or two noncritical accounts to demonstrate a proof-of-concept to management.
- C. Notify the development team of the discovery and suggest that input validation be implementedon the web application's SQL query strings.
- D. Request that management create an RFP to begin a formal engagement with a professional penetration testing company.
Answer: B
NEW QUESTION 12
A security consultant found a SCADA device in one of the VLANs in scope. Which of the following actions would BEST create a potentially destructive outcome against device?
- A. Launch an SNMP password brute force attack against the device.
- B. Lunch a Nessus vulnerability scan against the device.
- C. Launch a DNS cache poisoning attack against the device.
- D. Launch an SMB explogt against the devic
Answer: A
NEW QUESTION 13
A tester has captured a NetNTLMv2 hash using Responder Which of the following commands will allow the tester to crack the hash using a mask attack?
- A. hashcat -m 5600 -r rulea/beat64.rule hash.txt wordliat.txt
- B. hashcax -m 5€00 hash.txt
- C. hashc&t -m 5600 -a 3 haah.txt ?a?a?a?a?a?a?a?a
- D. hashcat -m 5600 -o reaulta.txt hash.txt wordliat.txt
Answer: A
NEW QUESTION 14
A client is asking a penetration tester to evaluate a new web application for availability. Which of the following types of attacks should the tester use?
- A. TCP SYN flood
- B. SQL injection
- C. xss
- D. XMAS scan
Answer: A
NEW QUESTION 15
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
- A. Badge cloning
- B. Lock picking
- C. Tailgating
- D. Piggybacking
Answer: A
NEW QUESTION 16
Click the exhibit button.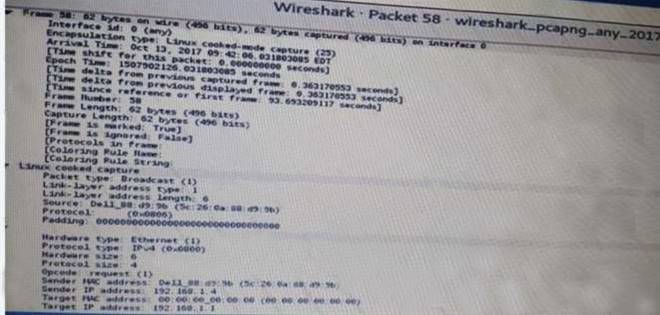
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network Which of the following types of attacks should the tester stop?
- A. SNMP brute forcing
- B. ARP spoofing
- C. DNS cache poisoning
- D. SMTP relay
Answer: B
NEW QUESTION 17
A penetration tester is checking a script to determine why some basic persisting. The expected result was the program outputting "True."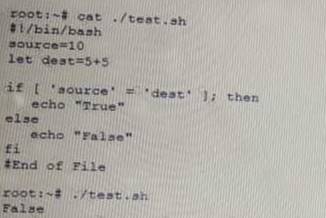
Given the output from the console above, which of the following explains how to correct the errors in the script? (Select TWO)
- A. Change fi' to 'Endlf
- B. Remove the 'let' in front of 'dest=5+5'.
- C. Change the '=" to '-eq'.
- D. Change •source* and 'dest' to "Ssource" and "Sdest"
- E. Change 'else' to 'eli
Answer: BC
NEW QUESTION 18
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.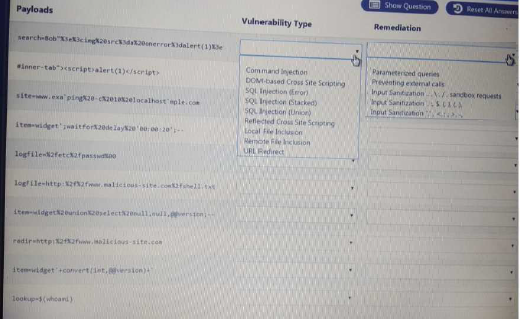

Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 19
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
- A. Script kiddies
- B. APT actors
- C. Insider threats
- D. Hacktrvist groups
Answer: B
NEW QUESTION 20
......
P.S. Easily pass PT0-001 Exam with 248 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared PT0-001 Dumps: https://www.certshared.com/exam/PT0-001/ (248 New Questions)